A Time to Review Cyber Liability Clauses
The threats from cybersecurity events and the possible liability for the disclosure of regulated, personal, sensitive, or contractually protected information has evolved over time. The legal requirements to review and respond to threats or attacks have also changed significantly over the past ten years. Cyber-threats companies presently face may not have existed ten, five, or even one year ago.
The graphic below depicts the number of zero-day events, or Common Vulnerabilities and Exposures (“CVE”) which have been identified and tracked by NIST over the past ten years[1]:
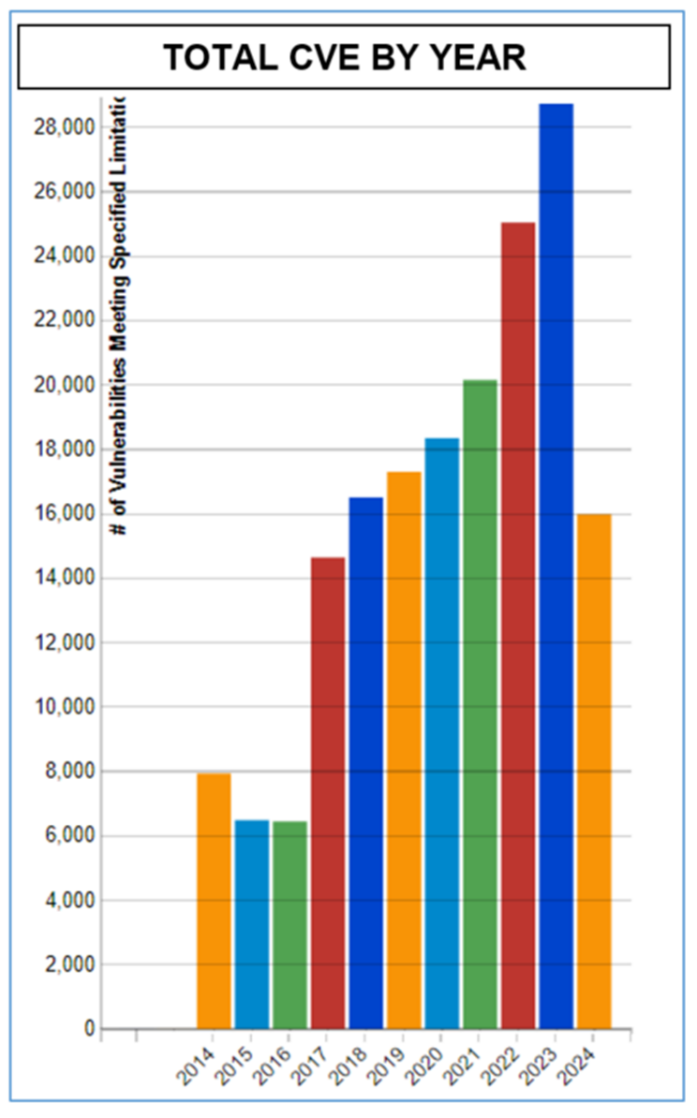
As the types and number of vulnerabilities evolve, the liability and notification clauses in contracts and agreements typically become stale over time. For example, a contractual cybersecurity requirement mandating certain types of security tokens or techniques to ensure security in 2014 may not apply in 2024, or worse may even create an increased chance of a cyberattack or exposure of data.
A few of the changes to the cyber risk landscape over the past decade include:
- Industry standard password security in 2014 may have only been eight to ten characters; today passphrases of sixteen characters or more are common.
- Microsoft’s Remote Desktop Protocol (“RDP”) may have been considered secure; today exposing Microsoft’s RDP to the Internet is considered a security issue.
- Nation-state actors were just beginning to arrive on the scene as a threat to business as was shown in the Sony hack by the Democratic People’s Republic of Korea (DPRK); now nation state actors are regularly identified as cyber attackers and threats to businesses and government services.
- Cloud computing was a relatively new concept in 2014; whereas now many platforms are offered as cloud services. The storage of information in the cloud can expose more information to malicious activity, but it may also increase security with automatic updates and security patches.
- Data privacy has been driven forward with the introduction of the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), as well as more than fifteen (15) other states which have adopted privacy legislation. Each one of these laws may change the cybersecurity requirements for data protection.
- In 2014 not all states had data breach notification laws; now all fifty (50) states, the District of Columbia, Puerto Rico, and Guam have data breach notification laws.
From just this short list of changes, we can see just how much the risk landscape is evolving.
These significant changes to the risk landscape over the past decade have likewise produced a number of changes to preferred contractual cybersecurity requirements. Companies should regularly review and assess cybersecurity clauses in their contracts to ensure they meet all current federal and state regulations and laws, and that all notification requirements meet any applicable federal or state notification requirements, including timing requirements. Such a review could be included as part of an annual cyber risk assessment. Maintaining relevant and current cybersecurity standards can save companies time and money in the event of an actual cybersecurity event.


